With the recent announcement of more than 500 million accounts impacted by a security leak, many Yahoo users have been changing their passwords. After all, that’s the official guidance. However, as ZDI’s Simon Zuckerbraun points out, a new password isn’t enough.
If you have a Yahoo account, chances are you’ve seen a notification that your account information has been stolen by attackers. You aren’t alone. According to public reports, more than half a billion accounts were impacted during a security leak in 2014. While it’s not known why it took Yahoo over 18 months to inform people, the notification from Yahoo CISO Bob Lord included the recommendation to change your password. While this is sound advice and a good first step, Zero Day Initiative (ZDI) researcher Simon Zuckerbraun found this step alone isn’t enough to protect your account.
Like many others, Simon received a notification that his account was included in the leak. Like many others, Simon logged in to his account and changed his password. He then opened his iPhone Mail application since he had configured the app to use his Yahoo account. He expected to be prompted for his new password and was more than a little surprised when he found it was not necessary. Even though he had changed the password associated with his Yahoo account, the phone was still connected.
Upon investigating, it became clear that Yahoo had issued a permanent credential to the device. This credential does not expire and is not revoked when the password changes. In other words, if someone already obtained access to your account and configured the iOS Mail app to use it, they would still have access to the account even after the password changes. What’s worse is that you would likely not even realize someone still has access to your email.
This presents a couple of different problems. First, steps beyond changing your password are not being clearly communicated from Yahoo. This could lead to a situation where millions believe they are protected even though they aren’t. Additionally, even if you are security conscious like Simon and want to review your activity and devices, it’s not easy to find. Associated devices aren’t listed under the “Account Security” tab at all. As shown in Figure 1 (below), the “Account Security” tab has no mention of associated devices.
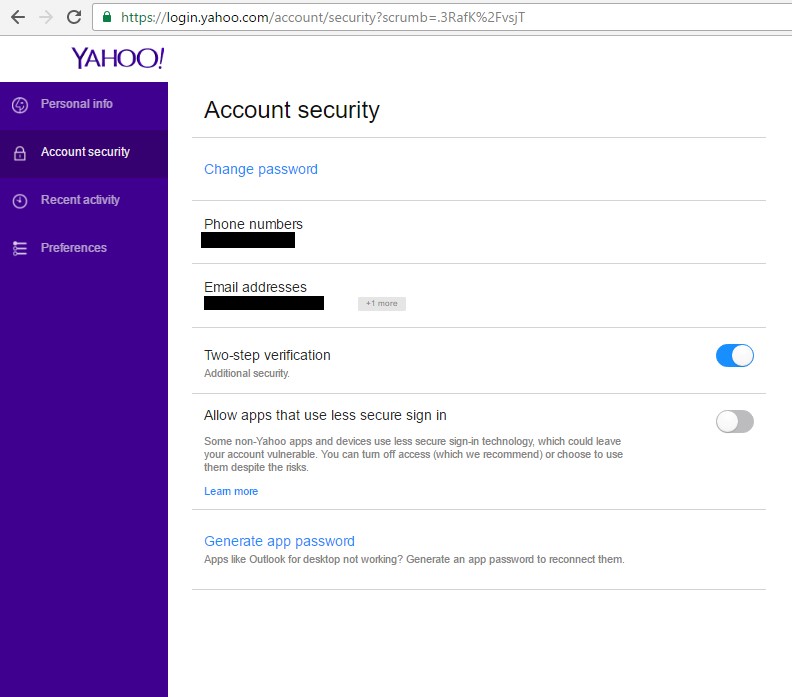
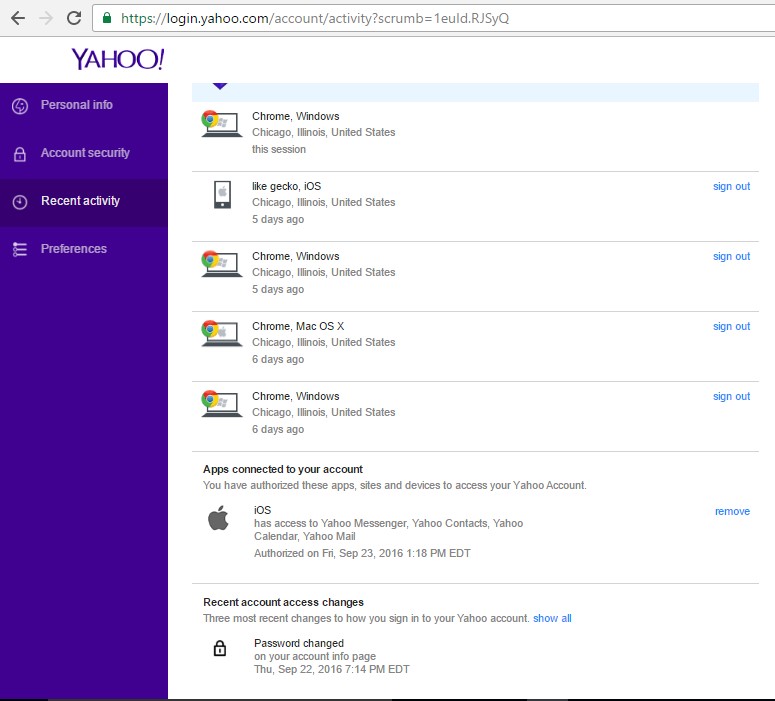
The setting actually exists under the “Recent Activity” tab (Figure 2). Here you are able to see which applications are connected to your account with an option to remove them. It’s also interesting to see the apps and devices are just listed by product name – in this case “iOS” – and the date authorized. It’s up to the user to figure out what is legitimate and what’s not.
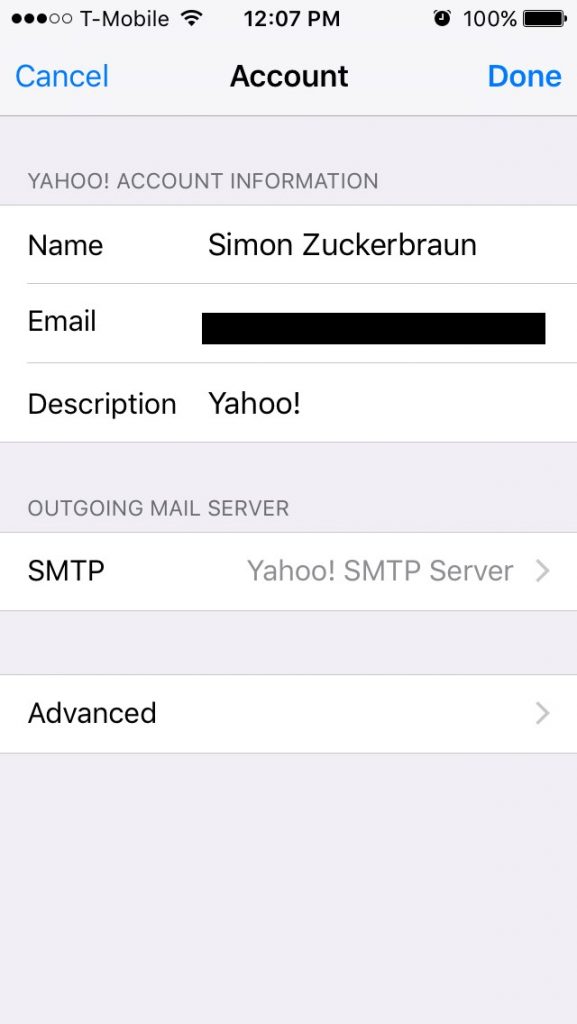
Looking at the phone settings (Figure 3) is of little help. Looking at the setting shows there is no option via the app to change the password. This is likely by design. When you set up your mail account on the device, it gets permanently credentialed until the credential is revoked through the server.
While it’s unfortunate Yahoo’s official advice for securing a hacked Yahoo account makes no mention of checking for or removing associated apps and devices, it definitely should be on your list. In fact, your list should look something like this:
- Change your password. This should still be your first step. It should always be your first reaction after an account compromise. If you reused the compromised Yahoo password with other online services, you’ll need to change it there as well. Have trouble remembering different passwords? Try a password manager like the Trend Micro™ Password Manager .
- Set up two-factor authentication (2FA) or use Yahoo’s Account Key. This will make it more difficult for attackers to access your information even if your password is compromised. Just don’t expect 2FA to reset your iPhone Mail app settings. You still need to go through the website to remove a device.
- Review your devices and activity. Understanding which devices access your account is key to finding unusual or unauthorized activity. You should specifically look for connected apps listed on the “Recent Activity” tab, as well as check the “Account Security” tab for active application passwords.
The steps users take after a leak notification often determine whether further account damage occurs. It’s unknown if the attackers will be able to decrypt stolen passwords or how they intend to use other leaked data. Regardless, if you change your password and review the associated devices, you’re less likely to be impacted. By understanding all the actions needed, you can exert some control over your account’s security.
